Navigating China's National Security Compliance: A Practical Guide for Foreign Enterprises
Navigating China's National Security Compliance: A Practical Guide for Foreign Enterprises
I. Introduction
China’s national security laws not only provide a solid legal basis for safeguarding national security, but also have a far-reaching impact on the operations of enterprises, especially foreign-invested enterprises.
As the nation’s fundamental law, the Constitution forms the bedrock of the national security legal system. The National Security Law, in turn, plays an overarching, comprehensive, and fundamental role, underscoring the importance of national security and the duty to safeguard it. The Criminal Law specifies criminal acts that jeopardize national security and their corresponding penalties, thereby forming a legal basis for countering acts such as subversion of state power, secession, and espionage. The Criminal Procedure Law complements this by specifically regulating special procedures and measures for handling cases related to national security.
China’s national security legal system presents a multi-layered nature across various domains, thereby establishing all-round, multidimensional security safeguards. In maintaining national political security, the National Intelligence Law, the Guarding State Secrets Law, and the Cryptography Law play a key role in ensuring the confidentiality of national intelligence work and the security of cryptography. Regarding national economic security, the Export Control Law has effectively safeguarded the country’s economic interests while fulfilling international obligations such as non-proliferation. As to military security, the National Defense Law, the Military Service Law, the People’s Armed Police Law, the Law on the Protection of Military Installations, the Law on National Defense Traffic, and the Maritime Police Law have together buttressed the development and security of the country’s military forces. Homeland security has seen the Land Boundary Law safeguard national sovereignty, security, and territorial integrity, while the Anti-Secession Law further ensure national unity and territorial integrity and counter secessionist forces. In the area of social security, the introduction of the Anti-Terrorism Law and the Law on the Administration of the Activities of Foreign Non-Governmental Organizations within the Country has enabled China to prevent and combat terrorist activities more effectively, while ensuring that the activities of foreign non-governmental organizations (NGOs) in China are in compliance with Chinese laws and regulations and do not pose a threat to national security and social order. Considering cyberspace security, China’s legal framework is anchored by the Cybersecurity Law, the Data Security Law, and the Personal Information Protection Law, which collectively form a legal basis for China to safeguard the cyberspace and ensure protection of personal information. Meanwhile, the Biosafety Law and the Nuclear Safety Law guard against risks and threats in their respective domains.[1] To safeguard the prosperity and stability of the Hong Kong Special Administrative Region, the Law of the Hong Kong Special Administrative Region on the Maintenance of National Security was promulgated and implemented in 2020.
The Anti-Espionage Law 2023 complements the aforementioned laws by equipping China’s national security organs (the “National Security Organs”, each a “National Security Organ”) with specific operational guidelines for the implementation of anti-espionage initiatives, including procedures for investigating, obtaining evidence, and dealing with espionage cases, thus ensuring the robustness and effect of national security laws. In addition to imposing post-facto penalties for espionage activities, this law integrates preventive provisions, such as the monitoring and prevention of potential espionage activities, a forward-thinking approach indicating the legal system’s emphasis on proactive strategies. Additionally, the enactment and enforcement of this law from part of China’s efforts to fulfill its international obligations to collaborate with the international community in countering transnational espionage, aligning with the obligations related to international cooperation and non-proliferation under the national security legal framework. In respect of regulatory documents, the Implementation Rules for the Anti-Espionage Law serve as specific operational guidelines for the Anti-Espionage Law 2023, detailing the concrete measures and procedures for anti-espionage work to ensure the law’s effective implementation.
The Provisions on Administrative Law Enforcement Procedures for National Security Organs focus on regulating the administrative procedures followed by National Security Organs in the enforcement of the Anti-Espionage Law 2023 and related legislation. Their promulgation marks a shift in China’s national security governance from a focus solely on substantive regulation to a dual emphasis on both substance and procedures.
II. Interpreting the Core Provisions of the Anti-Espionage Law 2023
1. Background of the Anti-Espionage Law 2023
The current Anti-Espionage Law 2023 evolved from the National Security Law enacted in 1993 (“National Security Law 1993”). The National Security Law 1993 primarily focused on the responsibilities of national security agencies in anti-espionage efforts and did not provide a comprehensive, foundational framework governing national security, resulting in a discrepancy between its name and its actual scope. Consequently, the National Security Law 1993 was repealed in 2014. After revisions, it was reintroduced as the Anti-Espionage Law (“Anti-Espionage Law 2014”).
However, the enactment of the Anti-Espionage Law 2014 was somewhat hasty, as it primarily focused on revising certain outdated provisions in the National Security Law 1993 (such as those involving concepts like the “people's democratic dictatorship”). As a result, the Anti-Espionage Law 2014 bears several shortcomings, including a narrow definition of espionage activities, inadequate security prevention mechanisms, insufficient administrative enforcement authority, relatively simplistic legal liabilities, and a lack of sufficiently rigorous norms for fair and lawful law enforcement. These issues necessitated further refinement.[2]
2. The Anti-Espionage Law 2023 and the Dual System of Legal Responsibility
Following the Sixth National People’s Congress’ decision to establish the Ministry of National Security, the National Security Organs, as a constituent department of the Nation Council, have assumed the dual nature of an administrative authority and an administrative law enforcement agency[3]. At the same time, the Criminal Procedure Law assigns to the National Security Organs the function of conducting criminal investigations[4].
Article 6 of the Anti-Espionage Law 2023 clearly states that the National Security Organs are the competent organs for anti-espionage work. In addition to the National Security Organs, various other governmental agencies, including the national security departments of the public security organs, the administrative departments in charge of confidentiality at all levels, and the defense departments of the military, also hold the authority to enforce law against criminal violations. In some cases, multiple governmental agencies may join forces in their law enforcement efforts, which poses higher requirements for corporate compliance. The promulgation of the Anti-Espionage Law 2023 has established a dual legal responsibility system for espionage, encompassing both “administrative offences and criminal offences”.
With regard to criminal liability of espionage, its substantive aspects are established primarily by the provisions of Chapter 1 of the Criminal Law’s specific provisions on crimes against national security. The procedural aspects are provided in principle by the Criminal Procedure Law, and further supplemented by the Provisions on Procedures for the Handling of Criminal Cases by the National Security Organs, which specifically addresses areas such as jurisdiction, disqualification, coercive measures, investigation, and execution.
Considering its administrative liability, the newly promulgated Anti-Espionage Law 2023 has provisions on the substantive, while the Administrative Penalty Law and the Administrative Compulsory Law regulate the procedural aspects, with the Provisions on Administrative Law Enforcement Procedures for National Security Organs making full-process, systematic provisions in terms of the subject of law enforcement, the applicable conditions, the approval hierarchy, the procedures of implementation, the timelines, etc. The Anti-Espionage Law 2023 likewise strictly limits the conditions, procedures, scope, and so forth of the exercise of the various law enforcement powers as well as the conditions, procedures, and scope of the exercise of such powers.
The establishment of the “administrative offence - criminal offence” dual legal responsibility system has transformed the original one-dimensional approach that addressed espionage acts only through criminal procedures. This new framework differentiates between administrative and criminal legal responsibilities according to the types of espionage acts and the degree of harm they cause, laying the groundwork for handling espionage acts outside the confines of criminal law, thereby facilitating a broader range of legal responses.
3. Highlights of the Core Changes to the Anti-Espionage Law 2023
The Anti-Espionage Law 2023 contains a total of 71 articles in six chapters, representing a comprehensive revision of the Anti-Espionage Law 2014, with 29 new articles added, 41 articles significantly altered, and almost every other article having undergone amendment and improvement to some extent. The most important amendment is Article 4, which provides the definition of espionage. The Anti-Espionage Law 2014 included the legal definition of espionage for the first time, but the provisions were not comprehensive, and the new Anti-Espionage Law has improved the definition by clarifying the connotation and scope of espionage.
Article 4 of the Anti-Espionage Law 2023 provides as follows:
For the purposes of this Law, an “Act of Espionage" refers to any of the following conducts:
(1) any activity that endangers the national security of the People's Republic of China (the “PRC”) that is carried out, instigated, or funded by an espionage organization and its agents, or carried out in collusion therewith by any domestic or foreign institution, organization, or individual;
(2) participating in an espionage organization or accepting any task from an espionage organization and its agents, or seeking refuge with an espionage organization and its agents;
(3) any activity carried out, instigated, or funded by a foreign institution, organization, or individual other than espionage organizations and their agents, or carried out in collusion therewith by any domestic institution, organization, or individuals, to steal, spy for, purchase, or illegally provide any state secrets or intelligence, or other documents, data, materials, or items of concern to national security, or to incite, entice, coerce, or bribe a state employee to defect;
(4) any cyber-attack, intrusion, interference, control, sabotage, or other such activity carried out, instigated, or funded by an espionage organization and its agents, or carried out in collusion therewith by any domestic or foreign institution, organization, or individual, which targets any state agency, entity involved with classified matters, or critical information infrastructure, among others;
(5) indicating any target for an enemy; or
(6) conducting any other espionage activity.
This law shall apply where an espionage organization and its agents engage in an espionage activity targeting a third country within the territory of the PRC or using any citizen, organization, or other conditions of the PRC, endangering the national security of the PRC.
The Anti-Espionage Law 2023 has expanded and refined the definition of espionage compared to the 2014 version, adding to the definition to include individuals defecting to espionage organizations, information related to national security, cyber-attacks, and legal sanctions against foreign spies for targeting third countries within China or using Chinese resources, reflecting a stricter stance on foreign espionage and also a timely update to meet the challenges of information technology.
4. Interpretation of Article 4 of the Anti-Espionage Law 2023 - Espionage
(1) Subjects of espionage: espionage organizations and their agents
As indicated in Article 4 Paragraphs 1(1) through 1(4), the acts of espionage are all related to espionage organizations and their agents. The identification of espionage organizations and agents of espionage organizations fall within the purview of the competent national security department of the National Council.[5]
Specifically, the term “espionage organizations” mainly refers to organizations set up by foreign governments with the aim of turning China’s public officials, people, and commercial organizations against China to infiltrate, steal, spy on, bribe, and illegally provide national secrets and information to national institutions and various organizations of our country, as well as to carry out subversive and destructive activities.[6] Examples include the Central Intelligence Agency (CIA) of the United States, MI6 of the United Kingdom, the Federal Security Service of the Russian Federation, Mossad of Israel, the Intelligence Headquarters of the Japanese Defense Agency, the National Intelligence Agency of South Korea, as well as the so-called “Military Intelligence Bureau of the Ministry of National Defense of China” and the so-called “National Security Bureau of China” in the Taiwan province, among others.[7] An “agent of an espionage organization” is a person who is instructed, commissioned, or financed by an espionage organization or its members to carry out, or to authorize or instruct others to carry out, activities that endanger the national security of the PRC.[8]
Enterprises may face potential allegations of involvement with “espionage organizations” or their agents. Such risks primarily stem from various operational factors, such as the complexity of employee backgrounds, exposure to sensitive information in commercial activities, handling of state secrets or critical technologies in technical exchanges, heightened scrutiny of funding sources, inadvertent facilitation of intelligence collection, and potential exploitation of cybersecurity vulnerabilities. These factors collectively contribute to an elevated compliance risk profile that requires rigorous internal governance mechanisms.
(2) Acts of espionage by joining an espionage organization or accepting missions from an espionage organization or its agents.
Paragraph 1(2) of Article 4 clearly defines "participating in an espionage organization or accepting missions from an espionage organization or its agents" as an act of espionage. Similarly, Article 110 of the Criminal Law, “Espionage”, stipulates that “[w]hoever endangers national security by committing any of the following acts of espionage shall be sentenced to fixed-term imprisonment of not less than 10 years or life imprisonment; if the circumstances are minor, he shall be sentenced to fixed-term imprisonment of not less than three years but not more than 10 years: (1) joining an espionage organization or accepting a mission assigned by the organization or its agent. […]”
For example, according to a case published by the Ministry of National Security, a Hong Kong-American citizen surnamed Liang went to the United States in 1983 to run a restaurant. In 1989, the United States signed a purported cooperation agreement with Mr. Liang and recruited him as an informant, and in the same year Liang became a naturalized United States citizen. The US espionage and intelligence agencies provided him with a fabricated CV, directed him to pose as a “patriotic philanthropist” by donating money to overseas Chinese associations while carrying out espionage and intelligence activities against China and spying on intelligence and turning back public officials. In April 2021, he was apprehended by the National Security Organs. In May 2023, Liang was sentenced to life imprisonment for the crime of espionage, with lifelong deprivation of political rights and confiscation of personal assets amounting to 500,000 yuan.[9]
In light of such risks, enterprises should strengthen background checks and behavioral monitoring of their employees and establish strict internal control mechanisms to prevent their employees from privately contacting, or accepting instructions or funding from, espionage organizations and their agents and using company resources to engage in espionage. In addition, enterprises should ensure that cooperation with overseas institutions and organizations is compliant and avoid establishing contact with any organizations and individuals identified as espionage organizations or their agents by the State Council’s competent department for national security. To mitigate risks in newly established cooperative relationships, enterprises should perform background checks and due diligence on perspective collaborators. Clarifying the legal responsibilities and obligations of all parties to a contract is also essential for effective risk prevention.
(3) Espionage with espionage organizations and their agents
The Anti-Espionage Law 2023 explicitly defines the act of defection to hostile organizations as espionage activity, a provision addressing frequently observed practices. In such cases, an individual involved typically demonstrates clear awareness that the receiving organization is deemed an espionage organization or agent thereof. Through various channels, these defecting individuals proactively establish contact to express intentions of either joining or accepting missions assigned by an espionage organization. Some even voluntarily provide sensitive national security information as bargaining chips to facilitate connections and negotiate terms with these hostile entities, thereby laying groundwork for collaborative activities that endanger national security. Recognizing the substantive social harm inherent in such actions, the revised law categorizes them as acts of espionage and specifies corresponding legal liabilities.
(4) Espionage against intelligence and national security information
Paragraph 1(3) of this Article 4 refers to Article 111 of the Criminal Law “stealing, spying on, trading in, or illegally supplying national secrets or intelligence for the benefit of persons outside the country”, where “intelligence” refers to matters relating to national security and interests which have not been publicized or which should not be publicized in accordance with the relevant provisions.[10] Where a people’s court hears a criminal case involving any theft, espionage, trading, or unlawful provision of information from abroad requires an appraisal of whether the information in question constitutes intelligence, the appraisal shall be made by the national secrecy department or the secrecy department of a province, autonomous region, or municipality directly under China’s central government.[11] Specifically, intelligence is identified by the National Secrecy Bureau and the Confidentiality Committee of the Central Military Commission.
The Anti-Espionage Law 2023 expands the scope of protected information by broadening the objects and scope of theft of secrets. In addition to “national secrets and intelligence”, the law now encompasses “other documents, data, information, and objects related to national security and interests”. Any acts of theft, espionage, trading, or illegal provision involving these newly included items are also deemed as espionage under the revised legislation.
In a case investigated by National Security Organs, Mr. Zhu, the former general manager of a domestic agricultural technology company colluded with a spy agency under the guise of “cooperative seed production” and illegally sold five types of parent rice seeds to the entity. After receiving abnormally high returns, he established a new company to continue large-scale sales of China’s proprietary premium parent rice seeds overseas. After appraisal by relevant national confidentiality departments, the seeds Mr. Zhu illegally provided to entities were classified as intelligence. As a result, the National Security Organs lawfully imposed criminal compulsory measures against Mr. Zhu. In January 2024, the Hefei Intermediate People's Court in Anhui Province sentenced Mr. Zhu to one year and six months in prison for the crime of “illegally providing intelligence to entities”. Additionally, the National Security Organs imposed administrative penalties on other 17 individuals involved in the case. Their further investigations into the relevant enterprises exposed long-term illegal sales of China’s premium seed resources overseas by certain domestic seed industry companies.[12]
The National Security Organs have also continued to be highly vigilant with regard to other suspected acts against national security and have performed public enforcement. At the end of the 2022, the Suzhou National Security Bureau, in conjunction with the Municipal Supervisory Bureau and the Bureau of Statistics, conducted public enforcement against Capvision. The consulting firm accepted substantial commissions from corporate clients to carry out consulting projects on sensitive domestic industries, and some of these clients had close relationships with governments, military, and intelligence agencies. By leveraging the pretext of expert consultation, the firm obtained information on key areas and important industries within China, such as policy research, national defense and military industry, finance and currency, high-tech, energy resources, medicine and health, etc., in some cases compromising national secrets and intelligence. As it was suspected of endangering national security, Capvision was mandated by the National Security Organs in accordance with the law to rectify the wrongdoings.
In view of the above cases, enterprises providing or commissioning consulting services should prioritize compliance with Paragraph 1(3) of Article 4 under the Anti-Espionage Law 2023. To ensure full compliance, enterprises also need to heed the relevant provisions of normative documents, such as the Measures on the Administration of Foreign-Related Investigations and the Measures for the Security Assessment of Outbound Cross-Border Data Transfer.
The relevant provisions of the Measures for the Administration of Foreign Investigations read:
Article 2 Foreign-related investigations as mentioned herein include:
1. Market and social investigations conducted under the entrustment or financial aid of any overseas organization, individual, or the agency in China of any overseas organization;
2. Market and social investigations conducted in cooperation with any overseas organization, individual, or the agency in China of any overseas organization;
3. Market investigations lawfully conducted by the agency in China of any overseas organization; and
4. Market and social investigations of which the materials and results are to be provided to any overseas organization, individual, or the agency in China of any overseas organization.
Article 9 Any foreign-related market investigation must be conducted by a foreign-related investigation institution and any foreign-related social investigation must be conducted by a foreign-related investigation institution with an approval of the authority concerned.
No overseas organization or individual may directly conduct any market or social investigation in China or through any institution without the license for foreign-related investigation.
The relevant provisions of the Measures for the Security Assessment of Outbound Cross-Border Data Transfer are:
Article 4 For an outbound data transfer by a data processor that falls under any of the following circumstances, the data processor shall apply to the national cyberspace administration authority for the security assessment via the local provincial-level cyberspace administration authority:
(1) outbound transfer of important data by a data processor;
(2) outbound transfer of personal information by a critical information infrastructure operator or a personal information processor who has processed the personal information of 1,000,000 individuals or more;
(3) outbound transfer of personal information by a personal information processor who has made outbound transfers of personal information of 100,000 individuals or more cumulatively or the sensitive personal information of 10,000 individuals or more cumulatively, since January 1 of the previous year; or
(4) other circumstances where an application for the security assessment of an outbound data transfer is required as prescribed by the national cyberspace administration authority.
Accordingly, consulting firms or enterprises commissioning consulting firms to conduct overseas-related market research must ensure that all market and social survey activities are performed exclusively by institutions possessing a Foreign-Related Survey License. Notably, social surveys additionally require approval from relevant regulatory authorities. Enterprises must refrain from collaborating with unlicensed entities, and organizations and individuals are prohibited from conducting market or social surveys directly within China. Furthermore, for the lawful collection, transmission, and use of sensitive information involving key sectors such as national defense, financial currency, high-tech industries, energy resources, healthcare, and biotechnology, compliance with the Security Assessment Measures for Cross-Border Data Transfer is mandatory. Entities must either submit national security risk declarations or conduct self-assessments to mitigate espionage-related compliance risks.
(5) Acts of espionage indicating targets for the enemy
Article 110 of the Criminal Law, which defines the crime of espionage, provides similar constitutive elements, namely, “[w]hoever endangers national security by committing any of the following acts of espionage shall be sentenced to fixed-term imprisonment of not less than 10 years or life imprisonment; if the circumstances are minor, he shall be sentenced to fixed-term imprisonment of not less than three years but not more than 10 years: […] (2) directing the enemy to any bombing or shelling target.” The Interpretation and Practical Guide to the Criminal Law of the People’s Republic of China by the Criminal Law Office of the Legislative Affairs Commission, Standing Committee of the National People’s Congress interprets this article as “[t]he ‘enemy’ referred to here mainly refers to hostile countries or enemy parties that are at war with us in wartime, and it also includes hostile state or enemy party that employ bombardment to attack the territory of our country in peacetime.”
It is worth noting, however, that Article 4, Paragraph 1(5) of the Anti-Espionage Law 2023 provides for the act of espionage to be an “attack”, and this characterization is semantically broader than Criminal Law’s formulation of the crime of espionage. Therefore, when a perpetrator commits an act of “attack” that does not fall within the narrower category of “bombardment”, there may not be a directly applicable criminal offence that corresponds to such an action, which, in some cases however, could fall within the scope of Article 4, Paragraph 1(5) of the Anti-Espionage Law 2023.
(6) Espionage in the form of cyber-attacks, intrusion, interference, control, sabotage, and other activities
The Anti-Espionage Law 2023 specifically clarifies in the definition of espionage that activities such as cyberattacks, intrusion, interference, control, and sabotage targeting national organs, classified units, critical information infrastructures, etc., in Article 4, Paragraph 1(d) are acts of espionage.
It should be noted that, as set forth by the law, the subject of cyber espionage must be related to espionage organizations and their agents, and if it is not the case for a cyber hacker and any other individuals who carry out cyberattacks or similar acts, they would not be deemed guilty of initiating espionage under the foregoing revised definition of the Anti-Espionage Law 2023. In such cases, their actions should be regulated by other laws such as the Public Security Administration Punishment Law, the Cybersecurity Law, and the Data Security Law.
(7) Espionage against third countries
Article 4, Paragraph 2 of the Anti-Espionage Law 2023 is newly added. Under this provision, any person who commits acts of espionage against a third country within the territory of China or by taking advantage of Chinese citizens or organizations, among others, and thus endangers China’s national security, is explicitly included in the scope of espionage and is subject to the Anti-Espionage Law 2023.
5. Interpretation of Articles 14 and 61 of the Anti-Espionage Law 2023 - not to illegally acquire or possess national secrets carriers
There are two articles in the Anti-Espionage Law that are aimed at preventing the unlawful acquisition and possession of national secrets: as foundation, Article 14 stipulates that “[n]o individual or organization may illegally obtain or possess any documents, data, materials, or items that are national secrets.” Article 61 further specifies legal responsibilities and penalties in this regard, stipulating that “for those who illegally obtain or possess any documents, data, materials, or items that are national secrets, or illegally manufacture, sell, possess, or use any specialized espionage devices, which does not yet constitute a crime, the National Security Organs shall issue a warning and impose an administrative detention of up to 10 days.” The term "illegally obtain or possess any documents, data, materials, or items that are national secrets" as used in the Anti-Espionage Law 2023 refers to the carrying or keeping of documents, data, and other items classified as national secrets by a person who either lacks the authority to access such national secrets or, though authorized to access the national secrets, is doing so without going through proper formalities.[13] The National Security Organs are empowered to impose administrative penalties under Article 61 of the Anti-Espionage Law 2023 in the case of illegally possession of the relevant items.
Therefore, in addition to the provisions of Article 4 of the Anti-Espionage Law 2023, which states that no one shall collude with subjects outside the country to steal, spy on, bribe for, or illegally provide national secrets, illegally acquiring or possessing national secrets in whatever form is also a violation of the Anti-Espionage Law 2023.
At the same time, the illegally acquisition or possession of any carriers of national secrets also violates the Law on the Preservation of National Secrets, and the National Secrets Bureau is empowered to enforce the law and deal with such misconducts. Article 57 of the Law on the Preservation of National Secrets provides that “[a]nyone who violates the provisions hereof and falls under any of the following circumstances shall be given disciplinary sanctions in accordance with the law and based on the seriousness of the case; any illegal gains shall be confiscated: (1) illegally acquiring or possessing any national secret carrier; ...... In cases where the actions outlined in the preceding paragraph do not constitute a criminal offense and for which disciplinary sanctions are not applicable, the administrative department of secret protection shall urge the authority or institution that the offender works for to deal with the offence". Article 54 goes on to provide that “[w]here an authority or institution fails to impose disciplinary sanctions in accordance with the law on a person who violates the national regulations on secret protection, the relevant administrative department of secret protection shall suggest it make corrections and, in the event of such authority or institution refusing to make corrections, shall submit the case to the superordinate authority or supervisory authority at the immediately higher level for the higher-level authority to take measures against such authority or institution, any responsible leaders bearing responsibility, and persons direct liable in the authority or institution in accordance with the law.”
Based on this, enterprises should establish and improve internal information security review regimes to ensure that all their employees are able to recognize the seriousness and consequences of illegally acquiring and holding national secrets carriers. Violations of confidentiality provisions should be promptly investigated and dealt with in order to safeguard the compliance of enterprises and the security interests of the PRC.
6. Interpretation of Article 16 of the Anti-Espionage Law 2023 - reporting of espionage acts
Article 16 of the Anti-Espionage Law 2023 provides that:
Any citizen or organization that discovers an act of espionage shall promptly report it to the National Security Organs; any such report made to a public security agency or any other state agency, or any organization shall be immediately transferred by that agency or organization to the National Security Organs for handling.
The National Security Organs shall publicly disclose their telephone number, address, web platform, etc., for receiving reports, promptly and duly handle any reported information, and maintain the confidentiality of informants.
At present, the channels for reporting espionage include: calling the National Security Organs via the 12339 report hotline; logging on to www.12339.gov.cn, the internet report acceptance platform of the National Security Organs and providing information; delivering letters to the National Security Organs; providing information in person at the National Security Organs’ offices; reporting to the National Security Organs through other State organs or agencies in the location where the informant is domiciled; reporting to the National Security Organs through the Ministry of National Security WeChat public account’s report acceptance function; other feasible ways to report.
In the event that a company is reported by any of its employees and therefore requested by the National Security Organs to cooperate with the investigation, it should promptly do so by providing the necessary information and assistance, and at the same time ensure that the investigation process complies with Chinese laws and regulations and the company’s internal policies.
7. Interpretation of Article 21 of the Anti-Espionage Law 2023 - construction projects in security control areas require permission from the National Security Organs to build trials
Article 21 of the Anti-Espionage Law provides that:
“Any new construction, renovation, or expansion project to be developed within the security control areas surrounding an important state agency, a national defense military-industrial entity, or any other important entity involving with classified information, or an important military facility, shall be subject to the granting of a permit for construction projects involving matters of national security by the National Security Organs.
All local people's government at the county level or higher shall fully consider national security factors and the demarcated security control areas and solicit the opinions of the National Security Organs when developing national economic and social development plans, territorial spatial plans, and other relevant plans.
The demarcation of security control areas shall take into account both development and security and adhere to the principles of scientific rationality and necessity, and it shall be carried out by the National Security Organs jointly with the agencies for reform and development, natural resources, housing and urban rural development, national secrets, and science, technology and industry for national defense, among others, as well as relevant military agencies, and reported to the people’s government of the relevant province, autonomous region, or municipality directly under the Central Government for approval and dynamically updated.
The National Security Organs under the State Council shall, in conjunction with relevant agencies, draft specific implementation measures for the permit for construction projects involving matters of national security.”
The National Security Law provides a national security review system in principle, and Article 59 of the law stipulates that “[t]he state shall establish systems and mechanisms for national examination and supervision, carry out national security examination on foreign investment, specific items, key technology, network information technology products and services, construction projects related to national security, and other significant matters and events, so as to prevent and neutralize national security risks in an effective way.”
Article 21 of the Anti-Espionage Law 2023 builds on this foundation by providing for permits for the construction and examination by National Security Organs. With regard to permits for construction projects involving national security elements, it is required that the delineation of security control areas be drawn up by the National Security Organs in conjunction with a number of governmental departments and submitted to the people’s governments of provinces, autonomous regions, and municipalities directly under the Central Government for approval or dynamic adjustment. In view of the fact that new construction, alteration, and expansion projects within security control areas all involve permits for construction projects involving national security matters, the provincial people’s governments are responsible for approving and dynamically adjusting the scope of the security control areas. By adopting this approach, governments can consider the perspectives of all stakeholders, ensuring that security control areas are appropriately designated based on necessity and practicality. This strategy allows for maintaining security without hindering progress and development in other areas.
Applicants for construction and examination permits for National Security Organs may apply for and make inquiries about such permits, and access relevant service guidelines, handling process guidelines, and other information at government service halls or service windows, via online processing, or through other means. The “Ministry of National Security Construction and Audit Permit Service Network” (www.jsxk.gov.cn) serves as an online platform that provides vital information and resources related to construction and audit permits administered by the National Security Organs. The platform has published the legal basis for the implementation of construction and audit permits, their handling process, and relevant norms and requirements. It also provides essential information such as acceptance venues for construction and audit permits and contact telephone numbers in various locations. Applicants may visit the website or contact the relevant authorities by phone for preliminary inquiries, and they may submit application materials for construction and examination permits through online channels or in-person at designated government service halls and offices. The National Security Organs will then process these applications, conducting the necessary reviews and rendering decisions on the applications in accordance with the law.[14]
III. Interpretation of the Provisions on Administrative Law Enforcement Procedures of National Security Organs and Compliance Guidelines for Enterprises
1. Legislative Background and Core Objectives
Amid the seismic shifts of the global geopolitical landscape and the accelerated iteration of the digital technologies, national security governance is facing multifaceted challenges. New types of national security risks, such as scientific and technological theft, cross-border data flow and the security of key industrial chains, have been surfacing with increasing diversity and complexity. Traditional law enforcement procedures have exposed limitations in addressing these new types of risks, such as inadequate coverage and technical adaptability. In addition, the ambiguous in authorization and non-transparent processes in traditional law enforcement also have implications on its effectiveness and efficiency.
The Provisions aim to achieve a re-balance between the protection of national security and the protection of the rights and interests of market players: on the one hand, the Provisions give the National Security Organs the power to enforce the law efficiently through mechanisms such as emergency expropriation and technical investigation. On the other hand, the Provisions also try to guarantee procedural justice through the design of rules such as “exclusion of illegal evidence” and “hearing procedure”. It can be said that, through the two-way rule design of “empowerment + procedural control”, the Provisions aim to help achieve a more efficient, transparent and fair national security law enforcement system.
2. Core Framework of Administrative Enforcement Procedures
The Provisions consist of seven chapters and 140 articles, encompassing investigation and evidence collection, hearing procedures, penalty decisions, enforcement procedures, review and litigation, etc., and, together with the relevant provisions of the Law of the People's Republic of China on Administrative Penalties (the “Administrative Penalties Law”), Administrative Coercion Law of the People's Republic of China, Law of the People's Republic of China on Administrative Reconsideration (the "Administrative Reconsideration Law"), and Administrative Procedure Law of the People’s Republic of China (the “Administrative Procedure Law”), as well as the related provisions of the law, forming the national security organs’ end-to-end “Investigation -Decision - Enforcement - Relief” administrative law enforcement framework.
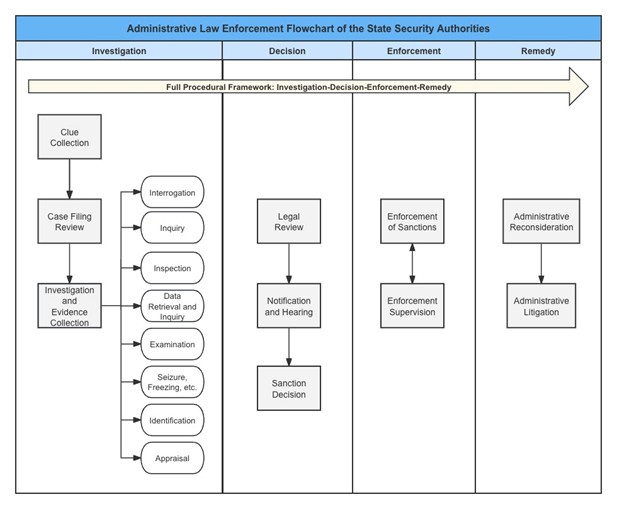
Table 1: Flowchart of administrative enforcement by national security organs
Businesses can focus on the following aspects of the enforcement process:
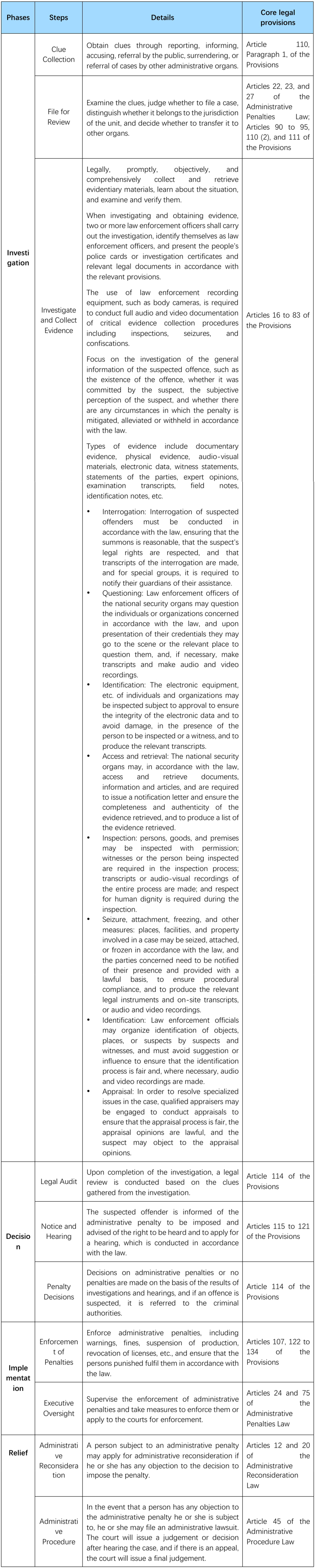
Table 2: Details of the administrative law enforcement process of National Security Organs
3. Procedural Analysis and Compliance Takeaways
To better navigate the primary stages of the administrative enforcement procedures undertaken by the National Security Organs, enterprises would be well-advised to pay close attention to the three critical stages of investigation and evidence collection, penalty decision and relief mechanism and their respective compliance elements, specifically:
(1) Inquiry Procedure: Conditions for Initiation and Response Strategies
Article 110 of the Provisions states that: “[t]he National Security Organs shall conduct case registration and investigation for the following circumstances: reports, complaints, tip-offs, public detentions of suspects by citizens, voluntary surrenders of suspects, cases transferred by other administrative or judicial organs, as well as illegal activities discovered by National Security Organs and their law enforcement personnel during national security work.”
Accordingly, the investigation process can be initiated through reports, complaints, tip-offs, voluntary surrender, and referral by other organs. In practice, investigations are often initiated by reports made by an employee or partner of an enterprise via relevant channels. Other common scenarios in which investigations are initiated include the transfer of clues involving national security risks to National Security Organs by other administrative or judicial authorities in the course of performing their duties, or the discovery of illegal risks by National Security Organs at their own initiative during surprise inspections.
Relevant laws and regulations confer on the investigated enterprises the legitimate right to take countermeasures in the face of administrative enforcement of national security. Among them, the Provisions, the Provisions on the Procedures for Handling Criminal Cases by National Security Organs, the Data Security Law of the People's Republic of China (the “Data Security Law”) and Anti-Unfair Competition Law of the People's Republic of China (the “Anti-Unfair Competition Law”) specify how enterprises may respond to investigations under the following provisions:
In the Provisions:
Article 17 The National Security Organs shall conduct investigations and gather evidence by two or more law enforcement officers. The law enforcement officers shall identify themselves as law enforcement officers and, in accordance with the relevant provisions, present their people’s police cards or reconnaissance certificates and the relevant legal instruments.
Article 28 When being questioned by law enforcement officers of the national security organs, suspected offenders shall provide truthful responses and have the right to refuse to answer irrelevant questions.
Article 30 When questioning a suspected offender, the statement and defense of the suspected offender shall be heard, and no heavier penalty shall be imposed on account of the statement or defense of the suspected offender.
A record of the enquiry shall be made.
If the questioning process is recorded on audio or video, the integrity of the audio- or video-recorded information shall be maintained.
If the suspected offender requests to provide written material on his or her own, he or she shall be permitted to do so. If necessary, the law enforcement officer may also ask the suspected offender to write on his or her own. The suspected offender shall sign or put his or her fingerprints at the end of the written material provided by him or her. For printed materials, the suspect shall sign or put his or her fingerprints on each page.
Article 46 Where, in accordance with the law, a staff member of a national security organ inspects or accesses relevant documents, data, information, or articles, he or she shall, with the approval of the person in charge of the national security organ at or above the municipal level of the district in which he or she is stationed, produce a notification of the inspection and access. The holder or custodian shall sign or stamp the notice.
Article 51 Where electronic data are retrieved as evidentiary material, reference shall be made to the relevant provisions of the Procedural Provisions for the Handling of Criminal Cases by National Security Organs, and the relevant State regulations shall be strictly observed.
In the Procedural Provisions for the Handling of Criminal Cases by National Security Organs:
Article 88 National Security Organs to the relevant units and individuals to retrieve electronic data, shall be approved by the person in charge of the National Security Organs, issued a notice of retrieval of evidence, indicating the need to retrieve the relevant information on electronic data, and notify the holder of the electronic data, the network service provider or the relevant departments to carry out. The unit or individual to be retrieved shall sign or stamp on the receipt of the notification, with the integrity check value and other methods of protecting the integrity of electronic data description. If necessary, the National Security Organs shall adopt audio or video recording and other ways to fix the content of the evidence and the forensic process to put forward the requirements, electronic data holders, network service providers or the relevant departments should be co-operative.
In the Data Security Law:
Article 38 Where any national organ needs to collect or use data to perform its statutory duties, it shall do so within the scope of its statutory duties and according to the conditions and procedures prescribed in laws and administrative regulations; any data it comes to know in the course of performing its duties, including personal privacy, personal information, trade secret, and confidential business information, shall be kept confidential and shall not be leaked or illegally provided to others.
In the Anti-Unfair Competition Law:
Article 30 Where any staff member of a supervision and inspection authority abuses powers, neglects duties, commits malpractices, or reveals any trade secrets known during the investigations, such staff member shall be subject to punishment in accordance with the law.
Based on the above laws and regulations, when subject to investigations by National Security Organs, enterprises may request that law enforcement officers conducting on-site inspections present identification and written notification, and that the scope of the inspection be recorded, thereby mitigating the risk of unauthorized searches or potential overreach during the investigation process.
In the case that any investigations involve data access, enterprises may request law enforcement officers to clarify the scope and use of the data under investigations, and if the data involves commercial secrets, they may also apply for confidential treatment in accordance with the relevant provisions of the Data Security Law and the Anti-Unfair Competition Law.
If personnel of an enterprise are summoned for questioning, in accordance with Article 28 of the Provisions, the person questioned has the right to refuse to answer irrelevant questions, i.e., the person being questioned is only required to answer those questions that are relevant to the matter under investigation; if law enforcement officials raise inquiries in the course of questioning that extend beyond the scope of the matter under investigation, the person being questioned may indicate to the law enforcement officials that “the question is not relevant to the case” and decline to provide an answer. In addition, although the Provisions do not explicitly provide for the presence of accompanying personnel during interviews[15], an enterprise may request the personnel being inquired to be accompanied by the enterprise’s in-house counsels or lawyers for the inquiry, so as to help the interviewed individual maintain composure and navigate the questioning process effectively. Furthermore, having professional accompaniment can ensure that any personal statements made by the individual are not misinterpreted as representing the enterprise’s position.
(2) Administrative Penalty Procedures: Safeguarding Rights and Avoiding Risks
The administrative penalty procedures of National Security Organs are crucial for the protection of the rights and interests of enterprises and the avoidance of risks. According to the Provisions, the types of administrative penalties imposed by National Security Organs include warnings, fines, orders to suspend production and operations, and revocation of relevant licenses. Among them, warnings are mostly applied to non-cooperation with National Security Organs’ law enforcement.[16] Fines are applicable in a much wider range of circumstances. If a person is subject to a fine, he or she shall pay the fine in accordance with the law within fifteen days from the date of receipt of the decision on the administrative penalty; if the fine is overdue, and such person fails to submit an application for deferment of payment or payment in instalments, the National Security Organs have the right to impose a late payment fine at the rate of three per cent of the amount of the outstanding fine amount per day.[17] In addition, the National Security Organs may, in accordance with the law, make recommendations to the relevant competent authorities on administrative treatment, such as ordering the enterprise to stop engaging in the relevant business or providing relevant services, ordering the suspension of production and business, revoking the relevant licenses or revoking the registration, and issuing a recommendation on administrative treatment. The relevant department shall, in accordance with the time limit and requirements, provide written feedback to the National Security Organs on the handling of the situation.[18] For enterprises, the full exercise of legal rights is the core of reducing the risk of penalties. Article 44 of the Administrative Penalties Law provides that “[b]efore deciding to impose administrative penalties, administrative organs shall notify the parties concerned of the administrative penalties to be imposed, and the facts, grounds, and basis upon which the administrative penalties are imposed and shall notify the parties concerned of their rights to state, defend, and request a hearing enjoyed in accordance with the law.” Articles 115 to 121 of the Provisions, which outline the procedures for a hearing before a decision on an administrative penalty is made by a National Security Organ, specify that for certain administrative penalties, the party subjected to the intended penalty may file an application for a hearing within five days of receipt of the notification of the penalty. If an application for a hearing is made, it is recommended that the applying enterprise submit written objections and pertinent evidence to ensure that relevant facts, opinions, and reasoning are substantiated, therefore facilitating a thorough review and consideration by the National Security Organs.
In addition, during the hearing process, enterprises may invoke the provisions of Article 20 of the Provisions on “Exclusion of Illegal Evidence” to reasonably question the legality of the evidence obtained by the National Security Organs through the investigation process, including collection of evidence, and to exclude evidence collected in violation of legal procedures or evidence obtained by means that violate mandatory provisions of the law and infringe upon the lawful rights and interests of others. For less contested cases, enterprises may also consider taking the initiative to put forward a rectification plan, in exchange for a reduction of punishment through the “Rectification Commitment”. These measures help achieve a balance between the protection of rights and interests and the compliance under the framework of law enforcement by the National Security Organs.
(3) Complaints and Redress Mechanisms
Enterprises may appeal and seek relief through administrative reconsideration and administrative litigation in respect of decisions on administrative penalties already taken by the National Security Organs.
Article 12, Paragraph 2 of the Administrative Reconsideration Law provides that “[i]f one has any objection to a specific administrative act of an administrative organ under vertical leadership, such as customs, finance, state taxation, foreign exchange management, or a national security organ, one shall apply to the competent department at the next higher level for administrative reconsideration." Article 20, paragraph 1, states: “[a] citizen, legal person, or any other organization deeming that an administrative action has infringed upon his or its legitimate rights and interests may file an application for administrative reconsideration within 60 days from the day on which he or it knew or should have known of such administrative action, except when the time limit for filing an application as provided for under the law exceeds 60 days.”
Article 45 of the Administrative Procedure Law provides that "[w]here any citizens, legal persons, or other organizations have any objection to the reconsideration decision, they may, within 15 days after receiving the decision, institute proceedings with a people's court. Where reconsideration organs fail to make a decision within the specified period, plaintiffs may institute proceedings with a people's court within 15 days from the date of expiration of the term for reconsideration, except where the law provides otherwise."
Accordingly, an enterprise may apply for reconsideration to a higher-level National Security Organ within sixty days from the date of receipt of the penalty decision; if, after the reconsideration, it still has objection to the outcome, it may file an administrative lawsuit at a people's court within fifteen days after receiving the reconsideration outcome.
Notably, according to Article 56 of the Administrative Procedure Law[19], in principle, the enforcement of an administrative act would not cease during pertaining litigation. Article 106 of the Provisions clearly provides that "[i]f the person subject to penalty applies for administrative reconsideration or brings an administrative lawsuit against the administrative penalty decision, the execution of the administrative penalty decision shall not be suspended, unless otherwise provided by law".
In practice, it is recommended that enterprises apply to the competent court for a "suspension of execution" in accordance with the exceptions stipulated in Article 56 of the Administrative Procedure Law, in order to avoid the impact of penalties such as suspension of business for rectification and freezing of accounts on its business operations.
4. Suggestions for Building a Compliance System for Enterprises
(1) Prevention: systems and training
In the framework of compliance management for enterprises, the cornerstone of an effective approach lies in proactive prevention. As a crucial stage, at the beginning of developing a compliance system, an enterprise normally needs to identify and attempt to manage potential risks, before it can be sure to develop an effective system along with relevant processes to avoid compliance problems.
Preemptive prevention does not only entail setting up a compliance system, but also highlight the critical importance of cultivating employees’ compliance awareness, which is the key to such approach of prevention. In the following section, we put forward relevant suggestions on the compliance system construction practice of foreign-invested enterprises in the stage of ex-ante prevention from the aspects of system construction and training system.
Firstly, for the purpose of ex-ante prevention, enterprises should first focus on the development of systems for security risk control.
With the deepening of globalization, the operational environment for companies has witnessed a steady increase in complexity. In recent years, particularly in areas involving cybersecurity, data protection, and cross-border information flows, foreign companies have faced intensifying legal, regulatory, and compliance risks.
For one thing, enterprises can establish and improve a data classification and hierarchy management system. One of the core objectives of national security compliance is to prevent the leakage of sensitive information and critical infrastructure risks. Data classification and management serve as a basic framework for compliance measures, as they facilitate the identification and categorization according to the degree of sensitivity of data.
At present, the Data Security Law of the People's Republic of China (the “Data Security Law”), the Personal Information Protection Law of the People's Republic of China (the “Personal Information Protection Law”), and the Rules for Data Classification and Rating of Data Security Technology have made requirements for data classification and management. Enterprises may classify their data in accordance with the above laws and regulations. Under the framework of such data classification, core data (e.g., relating to military, energy, geographic information, etc.) are required to be encrypted at the highest level, with access restriction and localized storage; important data (e.g., industry statistical data, technical patents, etc.) are required to be restricted from cross-border transmission, and security assessments of the important data are to be carried out on a regular basis; and for general data, basic security measures are applied to avoid wasting compliance resources.
In addition, classification and grading methods are in place for different data objects for different industries, such as the Principles of Industrial Data Classification for Intelligent Manufacturing, the Guidelines for Data Classification and Grading for Data Security Risk Prevention and Control in the Securities and Futures Industry, the Rules for Classification and Coding of Data Sets of Health Information, and the Measures for Data Classification and Grading in the Field of Civil Aviation, and so on. Building on these measures, enterprises can adapt their unique circumstances to specific business scenarios, refine the granularity of data classification, formulate more targeted data classification and grading specifications, and equip themselves with internal governance documents such as enterprise data classification and grading lists, important data and core data catalogue, etc., to improve the enterprise’s compliance management system in terms of data security.
For another thing, enterprises can focus on preventing security risks in foreign-related surveys. In addition to the lack of data classification and hierarchical management tools, in scenarios involving enterprises commissioning third parties to conduct market surveys, enterprises are also prone to heightened cybersecurity and data protection risks. In the case of Capvision[20] introduced above, national security was greatly threatened due to the company’s illegal acceptance of surveys commissioned from abroad.
According to Article 9 of the Measures for the Administration of Foreign-Related Surveys, “Foreign-related market surveys must be conducted through foreign-related survey organizations, and foreign-related social surveys must be conducted through foreign-related survey organizations after approval. Overseas organizations and individuals are not allowed to conduct market and social surveys directly within the country, nor are they allowed to conduct market and social surveys through agencies that have not obtained a foreign-related survey license.”
Accordingly, to develop compliance systems, enterprises should also establish a third-party cooperation compliance review mechanism to mitigate risks at the root. Specifically, enterprises need to be equipped with relevant qualification verification guidelines, strictly screen partners to identify those with investigation qualifications, and verify the qualifications of the chosen investigation agency by finding out whether the investigation agency has an investigation license in accordance with the law. Where conditions permit, enterprises can also specify in the commissioning contract the scope of data collection, authorization to use data obtained in the survey, and prohibitions on cross-border transmission of such data. For example, sensitive contents, such as geographic information of areas around military facilities and key industries, shall not be allowed to be probed by any third parties. The above system design or contractual agreements ensure that the business needs of an enterprise are met, while preventing passive involvement in acts endangering national security due to any irregular operation of a third party, ultimately achieving both business expansion and risk prevention and control.
Secondly, in the ex-ante prevention stage, improve the staff training system and enhance compliance awareness.
To develop a sound compliance system, an enterprise must ensure full understanding and strict compliance by its employees. To this end, training is equally crucial as the compliance system itself. Enterprises should put in place compliance training programs across different roles and departments to not only familiarize their employees with laws and regulations, such as the Anti-Espionage Law and the Data Security Law, but also ensure that they actively apply the relevant compliance requirements in their work.
In terms of training content, the recent focus should be on areas such as cybersecurity, data protection, commercial bribery, and intellectual property protection. In particular, for employees involved in cross-border business, training on cross-border compliance management should be strengthened to help them understand the differences in laws and regulations and compliance risks in different countries or regions.
Scenario-based safety training sessions are advisable as part of the training programs. During these sessions, enterprises may use real-world cases to strengthen employees’ risk alertness and compliance awareness. For example, through the introduction of the 2024 rice seed technology case[21] introduced thereinbefore, employees would understand the legal consequences of "unlawfully holding state secrets". Enterprises can also cultivate employees' resilience through regular simulation exercises. For example, by simulating crisis events such as data leakage, cyber-attacks, phishing emails, etc., they can help their employees familiarize themselves with the compliance management process and cultivate reliable decisions making in the face of unforeseen events, so as to reduce losses caused by potential compliance risks to the enterprise.
In conclusion, in the ex-ante prevention stage of corporate compliance system development, it is recommended that enterprises focus on both system development and employee training as the core to build a firm compliance defense and achieve bottom-up risk prevention and control.
(2) Responding to events: standardized processes and communication strategies
Under the framework of compliance management for enterprises, if the National Security Organs have opened administrative enforcement procedures against an enterprise, the enterprise’s response-in-action is the key line of defense for corporate compliance. As the core mechanism of risk prevention and control, the value of an efficient and legal mid-stage response lies in its ability to contain the compliance risks that have occurred within the scope of minimal impact through the rapid response and dynamic adjustment of standardized processes.
Notably, in response to unexpected regulatory enforcement, enterprises need to establish a dynamic balance between cooperating with regulatory requirements and safeguarding their rights and interests through strategies. How an enterprise responds to such emergencies serves in most cases as the critical determinant that turns crisis into opportunity while mitigating losses. This article attempts to provide practical guidance for enterprises seeking to build a scientific and professional incident response mechanism from the aspects of process standardization and communication strategy optimization.
First, in the ex-post response stage, foreign companies need to develop a standardized response process.
In response to the administrative enforcement of National Security Organs, enterprises may consider formulating an "Emergency Incident Investigation Response Manual" in advance to lay out specific guidance for taking actions during the whole process from the reporting of incidents to the closed-loop rectification. The manual should stipulate the composition of the rapid response team and division of tasks, recommending that the legal department take the lead in monitoring legal risks, the compliance department co-ordinate the deployment of internal resources, the IT department be responsible for technical forensics and data traceability, and the administrative department coordinate on-site reception and logistical support, thus forming a cross-departmental coordinated emergency response force.
More specifically, when facing evidence collection by law enforcement officers, enterprises must refer to the Document Provision Standards Checklist to define the scope of materials disclosable to authorities under laws such as the Anti-Espionage Law and Data Security Law. Such materials normally would include business licenses and anonymized operational reports. As a rule, data involving trade secrets or pending security assessments tend to necessitate internal review and declassification procedures. If law enforcement requests information beyond the permitted scope, enterprises should follow the pre-established Non-Standard Request Handling Protocol, which dictates that while cooperating with investigations, they must request officially stamped written notices from officers that evidence such request of information and promptly report the matter to the corporate compliance officer.
Second, in the ex-post response stage, foreign enterprises also need to use communication strategies to respond to law enforcement officers and at the same time make use of procedural provisions to provide legitimate and reasonable checks and balances.
In terms of communication with the regulators, enterprises should avoid confrontational responses and adopt the strategy of “co-operation with investigation + legal reservation”. This can be archived in three steps: the first step is to indicate an attitude of cooperation; the second step is to request law enforcement officials to explain the procedural propriety; and the third step is to negotiate and secure a reasonable timeframe for responding.
Throughout the communication process, it is essential to document the key dialogue points, refrain from using confrontational expressions, and involve legal advisors as witnesses if necessary. Employing these communication strategies allows an enterprise to show its respect for law enforcement authorities and at the same time safeguard its legitimate rights and interests, thereby preventing unnecessary legal conflicts arising from misinterpretation of information and avoid excessive confrontation which could potentially lead to intensified law enforcement.
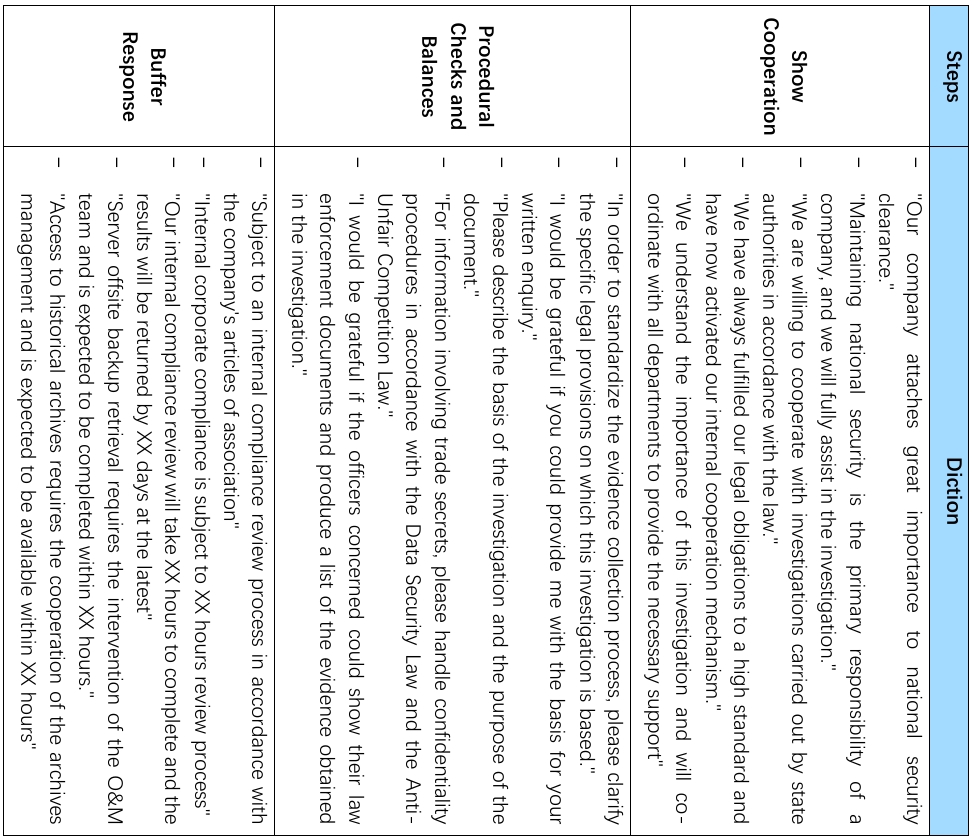
Table3 : Guidelines for Corporate Communication Protocols
(3) Ex post facto rectification: case review and system optimization
Under the framework of compliance management for enterprises, after-the-fact rectification can ensure that the corporate compliance system forms a closed loop of wind control. As the final line of defense in risk management, the core value of ex post facto rectification lies in turning exposed compliance loopholes into a driving force for system upgrading through systematic traceability and system regeneration.
After-action rectification not only involves the correction of individual problems, but also the holistic review of specific problems to enhance across-the-board compliance of enterprises. An enterprise’s thoroughness and promptness in post-event rectification has a significant bearing on the swiftness of its remediation efforts and efficacy of long-term governance after risk exposure. In the following section, we provide a practical roadmap for foreign enterprises to build and improve the post-event rectification system by way of case review and system optimization.
First, treat specific cases as learning opportunities for rectification and complete root cause analyses to identify potential issues and areas for improvement.
If the National Security Organs finally decide to impose administrative penalties on an enterprise, the enterprise should view the case as a basis for reflection and complete the rectification and review afterwards to form a closed-loop management. Enterprises subject to penalties should carry out Root Cause Analysis (RCA) of the cases in question and, if necessary, set up a review taskforce consisting of their legal affairs, compliance, business departments involved and potentially involve external lawyers to systematically trace the root causes of compliance risks and national security violations. During the process, they need to check business processes and compliance training records of the personnel involved against the violation specified in the penalty decision to ultimately form a Root Cause Analysis Report about the case.
Second, further update and upgrade internal risk control compliance mechanisms based on the results of the review.
Upon completion of the review process, enterprises may develop targeted improvement measures and revise internal control policies based on the Root Cause Analysis Report to prevent recurrence of similar incidents. Specifically, enterprises could establish a third-party “blacklist” system and implement dynamic evaluation mechanisms. The compliance department should continuously monitor regulatory developments and industry practices by regularly reviewing the latest national security laws, regulations, and representative enforcement cases to identify potential risk indicators. In the case that any third-party partner is found to have historical violations or current national security risks, enterprises should label its risks in internal systems and consider terminating such partnership if necessary.
Through after-action rectification, enterprises can resolve the risks associated with the incidents and potentially turn the crises into opportunities to improve their compliance capability, thus entering a virtuous governance cycle. This way, they may play a role in fostering sustained compliance and promoting a robust ethical business environment.
IV. Conclusion
The revision of the Anti-Espionage Law and the issuance of the Provisions mark the establishment of a dual-track national security governance framework in China—combining both substantive rules and procedural safeguards. In the face of an increasingly stringent enforcement environment, corporate compliance management is shifting from passive response to proactive risk prevention. Only by placing a high priority on national security compliance and embedding compliance requirements throughout the entire business chain can companies effectively navigate enforcement challenges and achieve sustainable growth amid a complex regulatory landscape.
[Note]
[1] See People’s Daily Online: “The Legislative Affairs Commission of the National People's Congress has released a report card on national security legislation achievements over the past decade”, http://cpc.people.com.cn/n1/2022/0425/c64387-32408102.html
[2] See National People’s Congress official website: “The Anti-espionage Law comes into force today! Wang Aili, Director of the Criminal Law Office of the Legal Affairs Commission of the Standing Committee of the National People's Congress, explains in detail”, http://www.npc.gov.cn/npc////c2/c30834/202307/t20230703_430418.html
[3] See Chen Weidong, “Reflections on the Administrative Law Enforcement Powers of National Security Organs”, Chongqing Three Gorges College, No. 5, 2004.
[4] See Article 4 of the Criminal Procedure Law: “The National Security Organs shall, in accordance with the provisions of the law, handle criminal cases endangering National Security and exercise the same powers and functions as the public security organs."
[5] Article 4 paragraph 2 of the Rules for the Implementation of the Counter-Espionage Law
[6] See “China’s Legal Public Education” WeChat public account (the official WeChat public account of the Ministry of Justice): “[4-15] Anhui: Stay away from espionage, protect national security”, https://mp.weixin.qq.com/s/9HC9_ 01b5NrPJXKAuR_PHA
[7] See Gilin People’s Government: “What Are Spy Organizations and Spy Organization Agents?” , http://www.jlcity.gov.cn/zt/zwzt/fjdzl/jczs/201810/t20181029_498295.html
[8] Article 4 paragraph 1 of the Rules for the Implementation of the Counter-Espionage Law
[9] See CCTV News: "National Security Department Unveils ‘Mask’ of US ‘Meritorious’ Spy, More Details Revealed", https://content-static.cctvnews.cctv.com/snow- book/index.html?item_id=3888103764853478216&t=1694389488735&toc_style_id=feeds_default&share_to=copy_url&track_id= 52692737-d8d7-4388-ab80-a0029c938914
[10] See Article 1 paragraph 2 of the Interpretations of the Supreme People's Court on Several Issues Concerning Application of Law for Trial of Cases of Stealing, Spying, Buying, or Unlawfully Supplying State Secrets or Intelligence for Entities outside the Territory of China
[11] See Notice of the Supreme People's Court and the National Administration of State Secrets Protection on Issues Concerning the Implementation of the "Interpretation on Several Issues Concerning the Specific Application of Law in the Trial of Cases Involving Stealing, Spying, Buying, or Unlawfully Supplying State Secrets or Intelligence for Entities outside the Territory of China"
[12] See CCTV official website: “Ministry of National Security Announces Typical Cases of Endangering China's National Security”, https://news.cnr.cn/native/gd/20240414/t20240414_526663821.shtml
[13] See Article 17 of the Implementing Rules of the Anti-Espionage Law
[14] See Official WeChat Account of the Ministry of State Security: “The new Counter-espionage Law particularly emphasize this important provision!”, https://mp.weixin.qq.com/s/0AXHc5r2spS3ww63DiVtFA
[15] See Articles 31 and 32 of the Provisions.
[16] See Article 107(1) of the Provisions.
[17] See Articles 131 and 132 of the Provisions.
[18] See Article 105 of the Provisions.
[19] See Article 56 The execution of the administrative act shall not be suspended during proceedings, except under any of the following circumstances:
1. where the defendant considers that it is necessary to suspend the act;
2. where the plaintiff or an interested person applies for suspension of the act and the people's court rules that such administrative act shall be suspended as, in the opinion of the people's court, the execution would cause irremediable losses and the suspension of the act would not harm the national interests and public interests;
3. the people's court rules that such administrative act may severely damage the national interests and public interests; and
4. where suspension of execution is required by the provisions of laws or regulations.
If the party concerned is dissatisfied with the ruling on suspension or not suspension, it may apply for reconsideration once.
[20] See Case of Capvision Company: A company was investigated and dealt with by the National Security Organs for accepting overseas commissioned investigations in violation of the law. For details of the case, see the Ministry of national security Circular: [Case 10 of "Innovation Leads - National Security Sharpens the Sword"] (https://mp.weixin.qq.com/s/FBMMEIP5ZUJOJ4y5HZXRrg).
[21] See CCTV report, "Ministry of National Security Announces Guiding Cases of Endangering China's National Security", https://news.cnr.cn/native/gd/20240414/t20240414_526663821.shtml









